Patch Management for SMB
Patch Management
In May 2017, WannaCry exploited a vulnerability that had been patched in supported versions of Windows in March. Since so many systems are not managed and updated on a routine basis, this turned into a crisis claiming over 200,000 victims in 150 countries, including factories, hospitals, small businesses and schools. The ransomware was further assisted by computers running unsupported operating systems (Windows XP) that no longer receive security updates from Microsoft. Due to the extent of Wannacry’s damage, Microsoft did eventually release a special update for Windows XP in May: after the attacks occurred and more than two months after supported versions of Windows received the update.
The attackers behind WannaCry are not unusual in targeting known vulnerabilities that have fixes. The third most common exploit seen in the first half of 2016 took advantage of a vulnerability that was identified and patched in 2010!
Unsupported Versions of Operating Systems and Applications
Microsoft maintains support lifecycles for versions of Windows and applications like Microsoft Office. The product lifecycle includes these stages: Mainstream Support, Extended Support, and End of Life

Microsoft Office follows a similar lifecycle policy, but Microsoft Office 365 is covered under continuous support and the new “Modern Lifecycle Policy” which is dependent on the duration of the customer’s agreement with Microsoft. Software may receive a higher cadence of updates under the Modern Lifecycle policy and Microsoft will give 12 months’ notice prior to any end of life for products without replacement.
Security Patching and Updates
Software updates fall under three categories:
- Security Patches. Security Patches address and protect against known vulnerabilities.
- Hotfixes. Hotfixes fix non-security problems in the software. These are not available after mainstream support ends except under expensive enterprise paid support agreements.
- Service Packs. Services Packs are bundled packages of all security updates and hotfixes, plus additional fixes, available at the time of release. The Service Pack becomes the new baseline for subsequent security updates and computers without the latest service pack may fail to install future patches.
For Microsoft products including Windows and Office, patches are released every month on the second Tuesday, known affectionately by IT professionals as “Patch Tuesday”. Unless there is an active exploit in the wild requiring an emergency patch release, security patches are held and released on this day to help businesses plan their deployments and maintenance windows.
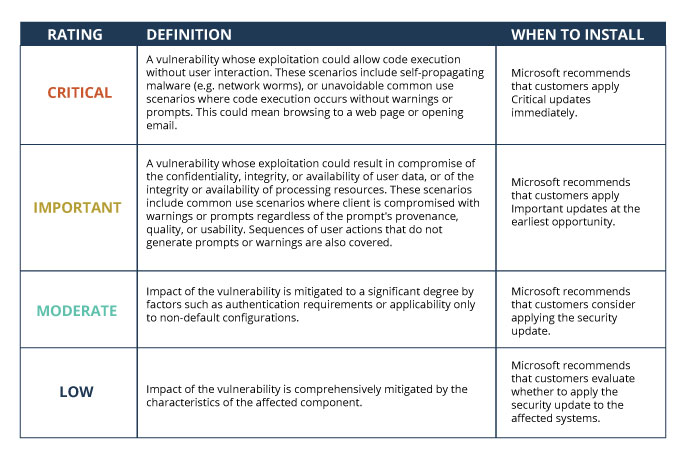
Security Patches are ranked according to severity level. The higher the severity level, the sooner you should install the patch:
For home computers, consumers often depend on Windows Update to automatically install security updates and hotfixes as they are released. Windows Update does not check for or apply patches for other software like Adobe Reader or Java Runtime Environment that are also targeted by attackers. For non-Microsoft applications, there may be an option within the application to check for updates. Turning on automatic updates eliminates the user’s need to manually check for and understand different security patches, and reduces the chance of the computer being vulnerable to attacks. However, this approach is insufficient for business computers because users with administrative privileges can turn off Windows Update, additional network traffic is created by multiple applications checking for updates, different software vendors may release patches at different times causing multiple employee disruptions, and there is no centralized reporting to ensure compliance with security policies. If a security patch fails to install, the user is often unaware there is a problem and the system remains vulnerable.
Businesses of all sizes should centrally manage their patch deployments and installations. This process is often achieved with a client agent that runs on the employee’s computer to check the status of installed patches and then reports into the management system to check for new IT-approved patches. If the employee’s computer encounters any issues installing the patch, such as insufficient space or does not meet the prerequisites, the client agent reports this information back to IT to be resolved. Selecting, configuring, and managing a centralized patch deployment tool may require investment in a server and skilled IT administrator. For small businesses, a trusted managed services provider can provide these services more efficiently, report on security compliance, and help your business plan when to upgrade or replace aging computers.
